Содержание
About ICS
Internet Control Server (ICS) is multifunctional network solution equiped with a set of over 80 functions sufficient for keeping network operations safe and sound for a typical enterprise.
Being a universal Internet gateway Internet Control Server is engineered upon FreeBSD operating system. ICS supersedes typical Unified Threat Management solutions by providing full set of corporate network security services, elaborate traffic and user accounting, access control, mail, proxy, file, jabber and Voice over IP servers all sharing common control, reporting and configuration. ICS acts as a smart router, plugged between your corporate nertwork and the Internet, leaving you network safe, controlling traffic and enforcing your corporate use and security policy.
Key functions of ICS
| Universal internet gateway | Supports of multiple Internet connection types: Ethernet, Wi-Fi, 3G, PPTP, PPPoE, L2TP. Supports VLANs and DMZ. Works with several ISP at once, supports PPPoE/PPTP VPN for corporate users, tunnels traffic via GRE/IPIP VPN tunnels with IPSEC PSK encryption as well as Open VPN. Supports terminal clients. Routes IP traffic. Provides DNS, DHCP. |
| Access control | User authentication by IP address, MAC, login/password pair, terminal server user authentication. Authentication via Active Directory, via local software agent, via VPN connections (PPPoE, PPTP) and pre-paid cards. Full Windows network integration. Layer 7 filtering, content filtering, traffic categorization by SkyDNS, Kaspersky Web Filter, https filtering. |
| Network security | Network firewall. Built-in antiviruses selection of Dr.Web, Caspersky, ClamAV. Incoming and outgoing traffic inspection. Data loss protection module to keep your confidential information inside, ICQ interception, Network address and port translation (NATPT), DMZ support. Network intrusion prevention system (NIDS/NIPS), raid-1 support for increased system stability. |
| Communication and network support | Proxy server, mail server with SPAM filters, DNS, DHCP, Web, FTP, IPSEC encryption, multiple remote office secure interconnection via encrypted tunnels. |
| Traffic accounting and network visibility | Traffic and access accountng by user, user groups, address groups, network interfaces, sites and URLs, files, protocols, MIME-types, timestamp, traffic source. Netflow parsing to obtain traffic statistics from external routers (Cisco, Juniper and more). |
| File and web servers | File storage with HTTP/FTP access. Windows network neighborhood (CIFS/SMB) access. File storage uses reliable ZFS file system with RAID 0/1 support and fault tolerance. Fully functional web server with PHP support and MySQL database with unlimited number of web sites deployed. DNS server included. |
| Proxy server | Allows to obtain precise web usage statistics, allow/deny specific users to specific web sites and URLs within sites. Traffic and channel utilization optimized by 10-30%. |
| Voice over IP | Allows to put up fully functional corporate IP telephony gateway with IVR, incoming and outgoing call filtering and forwarding, reporting. Support of SIP and IAX protocols. |
Working principle
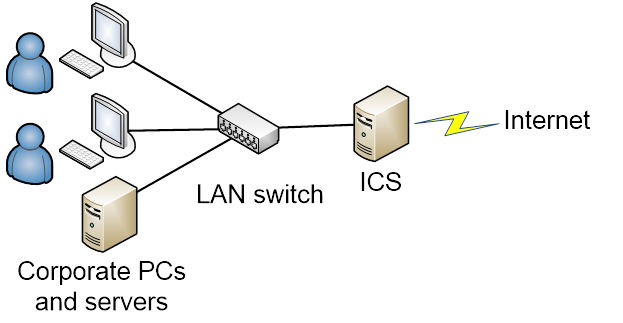
ICS densely integrates a well-chosen set of solutions on a single platform. It also contains DBMS storing all configuration data, traffic statistics, reports, users, rules, along with middleware responsible for logic uniting all parts of the system. ICS is designed to address all needs of a typical enterprise related to connection of corporate network to the Internet. ICS turns a general computer into powerful Internet router and gateway supporting all corporate communications. ICS middleware makes all its components operate in concert, minimizing configuration effort to virtually zero, keeping your network operation secure, manageable and visible from convenient graphical interface. ICS is typically installed at an x86 (32 or 64bit) computer with two or more network interfaces. Part of these interfaces is designated as external and connects to ISP equipment, the others are internal and links to corporate network (office LAN switch with connection to other client’s computers in the simplest topology).
ICS can support much more complex topologies, including DMZ, virtual LANs, tunnels between remote offices, multiple ISPs, complex switching and routing in corporate network, etc. Every corporate user should be configured at ICS (or imported from domain controller). Every user is assigned a portion of network resources, addresses and authentication scheme. Various authentication schemes can be used simultaneously. Users can be managed individually or collectively as user groups. IP addresses can be configured statically or delegated via built in DHCP service or by means of automatically configured tunnels with PPTP or PPPoE. Every user can be associated with resource quotas – for resource consumption, e-mail addresses, etc. Special rights, like administrator of a particular group can also be delegated to a user. A user can even be associated with an account, which measures resource consumption with user payments.